Are you aware that there are different types of hackers that can exploit your security weaknesses on the internet? This is why it’s important for xou to understand the distinctions between these hackers, how hacking operates, and ways to protect against it.
Hacking is the process of taking advantage of flaws in computer systems, networks, or software to gain unauthorized access or control. It involves manipulating systems and data to accomplish particular goals, which can differ greatly based on the hacker’s intentions.
Also read: Dangers of Using Free WiFi Near Me
Who is a Hacker?
A hacker is an individual who possesses advanced technical skills and knowledge in the field of computer systems and networks. Hackers employ their expertise to gain unauthorized access, manipulate data, or exploit vulnerabilities in digital systems. However, it is essential to distinguish between different types of hackers based on their intentions and ethical boundaries.
14 Different Types of Hackers
1. Black Hat Hackers:
Black hat hackers engage in malicious activities and operate outside the boundaries of the law. Their primary goal is personal gain, which can include stealing sensitive data, causing damage, or perpetrating financial fraud. Black hat hackers exploit vulnerabilities for their own nefarious purposes and are a significant threat to individuals, businesses, and governments worldwide.
2. White Hat Hackers:

White hat hackers are one of the types of hackers also known as ethical hackers or security researchers, are individuals who use their skills for positive purposes. They work with organizations and obtain permission to identify vulnerabilities in systems and networks. White hat hackers play a vital role in enhancing security by exposing weaknesses and helping organizations patch them before malicious actors can exploit them.
Also read: Website to IP lookup – How to lookup a website’s IP address
Read also: A Comparative Analysis of CyberGhost VPN, Avast VPN, and NordVPN
3. Blue Hat hackers:
Blue Hat hacker refer to a security professional or hacker who is invited by an organization to test and evaluate the security of its systems. It is regarded as penetrationtester. Unlike Black Hat hackers, who exploit vulnerabilities for malicious purposes, and White Hat hackers, who work to secure systems and protect against threats, Blue Hat hackers often have a specific focus on assessing and improving the security of a particular organization or system.
4. Green Hat hacker:
The term Green Hat hacker refers to newbies who passionate about hacking and are just learning how to hack. It sometimes informally used to refer to someone who is relatively new or novice in the field of hacking or cybersecurity.
The color-coded terminology (like blue hat, green hat) is not as standardized as white hat and black hat, and the interpretation may vary depending on the context. In some cases, it could be used playfully or informally to describe someone who is in the early stages of learning about hacking or cybersecurity.
5. Gray Hat Hackers:
Gray hat hackers fall in between white hat and black hat hackers. They may discover vulnerabilities without obtaining explicit permission, but their intent is not necessarily malicious. Often, gray hat hackers notify system owners about the vulnerabilities they find. However, their actions still raise ethical concerns since they operate without proper authorization.
6. State-Sponsored Hackers:

State-sponsored hackers are individuals or groups backed by a nation-state or government agency. They possess significant resources, and advanced techniques, and work towards achieving political, economic, or military objectives. State-sponsored hackers engage in activities such as espionage, intellectual property theft, and sabotage of critical infrastructure. Their actions have far-reaching implications, impacting national security.
Read also: Complete Guide to Virtual Private Server (VPS)
7. Script Kiddies:

Script kiddies are individuals with limited technical knowledge who rely on pre-written scripts or hacking tools to carry out their activities. They often lack a deep understanding of hacking techniques and primarily rely on automated tools to exploit vulnerabilities. While script kiddies may not pose a significant threat compared to more sophisticated hackers, their activities can still disrupt systems and compromise security.
Also read: 6 Effective Methods to Track IP Address
Read also: Funny WIFI Names – Meaning & List of 50 Funny WIFI Names
8. Hacktivists:

Hacktivists are one of the types of hackers who are politically or socially motivated. They use their skills to target systems and networks to promote a cause or protest against organizations or governments. Hacktivists often deface websites, leak sensitive information, or disrupt online services to raise awareness about their chosen issues. Though their intentions may be driven by activism, their actions can have severe consequences and often result in legal ramifications.
Also read: Tips for Mobile Application Security
9. Malware Writers:

Malware writers specialize in creating malicious software, such as viruses, worms, Trojans, ransomware, and spyware. Their objective is to compromise systems, steal sensitive information, or gain unauthorized access. Malware writers constantly evolve their techniques to bypass security measures, posing a significant threat to individuals, businesses, and even governments.
Also read: How to Prevent Facebook Hack – Complete Guide
10. Social Engineering Hackers:
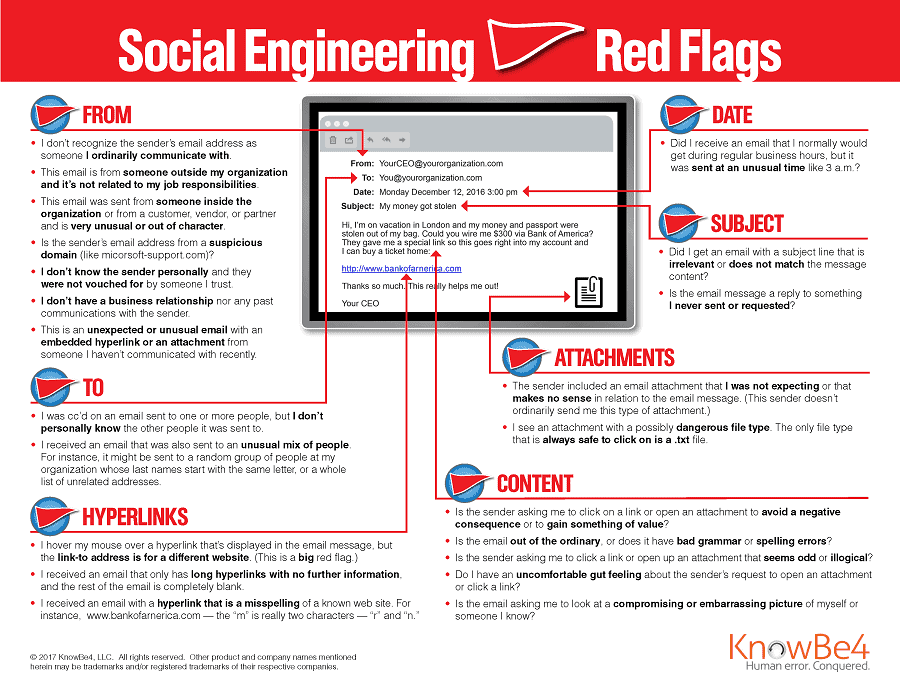
Social engineering hackers specialize in manipulating people through psychological techniques to gain unauthorized access to information or systems. They rely on tactics such as pretexting, phishing emails, impersonation, and exploiting human trust to deceive individuals. Social engineering attacks are particularly dangerous as they exploit the weakest link in any security system.
Related: How to Prevent Social Engineering
11. Phreakers:
Phreakers are one of the types of hackers that focus on manipulating and exploiting telecommunications systems, particularly phone networks, and services. Their activities involve making free calls, tampering with phone systems, intercepting communications, or even engaging in phone fraud. While the prominence of phone networks has diminished with the rise of the internet, phreakers continue to find new ways to exploit telecommunications infrastructure.
How Hacking Work
Hacks involve a variety of techniques and methodologies depending on the target and the hacker’s objectives. Common hacking methods include exploiting software vulnerabilities, leveraging social engineering tactics, and utilizing malware or malicious code. Successful hacks often rely on a combination of technical skills, ingenuity, and knowledge of system weaknesses.
Also read: 15 Best Free VPN for Android, iPhone and Computer Users
how hacking works:
- Gathering Information: First, the hacker begins by gathering information about the target. This phase involves identifying potential vulnerabilities, network architecture, system configurations, and potential entry points.
- Scanning: Once the hacker has gathered information, they use various tools and techniques to scan the target system for weaknesses. This could involve port scanning, vulnerability scanning, or network mapping to identify potential points of entry.
- Exploitation: After identifying vulnerabilities, the hacker attempts to exploit them to gain unauthorized access. This could involve exploiting software flaws, using default or weak credentials, or tricking users through social engineering techniques.
- Gaining Access: Once a vulnerability is successfully exploited, the hacker gains access to the system or network. They may establish a persistent presence to maintain access for future exploits or data exfiltration.
- Privilege Escalation: In some cases, hackers may seek to elevate their privileges within the system to gain administrative control. This allows them to access sensitive data, modify configurations, or execute malicious code.
- Maintaining Persistence: To ensure continued access, hackers often employ various techniques to maintain persistence within the compromised system. This could involve installing backdoors, creating hidden user accounts, or manipulating system processes.
- Covering Tracks: Skilled hackers aim to cover their tracks to avoid detection. They erase logs, modify timestamps, and remove any evidence of their activities to hinder forensic analysis and make it difficult for security professionals to trace their actions.
Also read: How to know and What to do if your Phone is Being Monitored by Spyware
Top 5 Most Famous Hackers of All Time
In the realm of cybersecurity hacking, there are some people who history will never forget because of their exceptional hacking skills. Below are the top famous hackers that have influenced the ever-evolving field of cybersecurity.
1. Adrian Lamo:

Adrian Lamo was a highly skilled hacker known as the “Homeless Hacker.” He gained attention for hacking into the systems of companies like Microsoft, Yahoo!, and The New York Times. However, Lamo became widely recognized for his involvement in the arrest of Chelsea Manning, formerly known as Bradley Manning, who leaked classified documents. Lamo reported Manning’s actions to authorities, leading to a controversial legal case. Lamo’s story raises complex ethical questions surrounding the role of hackers in exposing wrongdoing and the responsibility they bear for their actions.
2. Kevin Mitnick:

Kevin Mitnick is perhaps one of the most well-known hackers in history. In the 1980s and 1990s, he gained infamy for infiltrating numerous high-profile computer systems, including those of major corporations and government agencies. His hacking skills were unparalleled, and his ability to manipulate people through social engineering was legendary. Mitnick’s actions led to his arrest in 1995 and subsequent prison sentence. However, after his release, he transformed into a respected cybersecurity consultant and author, using his experiences to educate others about the importance of security.
Also read: Internet Security Threats to Watch for
3. Anonymous:

Anonymous is a decentralized hacker collective that rose to prominence in the early 2000s. The group, characterized by its Guy Fawkes masks and online presence, targeted organizations and individuals engaged in activities it deemed unethical or unjust. Anonymous launched cyber attacks, defaced websites, and leaked sensitive information. While controversial and often engaging in illegal activities, the group aimed to expose corruption and promote freedom of speech. Anonymous demonstrated the power of collective action in the digital age and sparked debates about the ethics and impact of hacktivism.
4. Gary McKinnon:

Gary McKinnon, a British hacker, made headlines for what has been dubbed “the biggest military computer hack of all time.” McKinnon infiltrated numerous U.S. military and government systems, searching for evidence of UFOs and suppressed technologies. His actions caused significant disruption and drew attention to vulnerabilities in these critical systems. McKinnon fought against extradition to the United States, arguing that he was on a quest for truth and should be protected as a whistleblower. His case shed light on the challenges of balancing justice and the pursuit of knowledge in the world of hacking.
Also read: What is Default IP Address And How to Use it – 192.168.0.1
5. Kevin Poulsen:

Kevin Poulsen, also known as “Dark Dante,” gained notoriety for his hacking activities in the 1980s. He hacked into telephone systems, specifically targeting radio stations to manipulate contests and win valuable prizes. Poulsen’s activities caught the attention of law enforcement, leading to his arrest. Following his conviction and release, Poulsen transformed his skills into a successful career in journalism and became an editor at Wired News. His journey demonstrates the potential for hackers to use their knowledge for positive contributions to society.
Also Read: 10 Signs of a Malware Infection on your Computer
8 Hacking Prevention Methods
Digital security threats are prevalent today because of how connected we are, so, it is important to understand how to prevent hackers and their hacking techniques.
Below are 10 ways to prevent hacking and safeguard your online presence.
Suggested read: 6 Password Safety Tips you Should Never Ignore
1. Use Strong and Unique Passwords :
One of the most important safety tips to prevent hacking is to create strong and unique passwords. Use a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information and never reuse same password across multiple platforms.
Also read: 8 Top Web Hosting to Choose for Your Business
2. Enable Two-Factor Authentication (2FA):
Two-factor authentication adds an extra layer of security by requiring an additional verification step, usually through a unique code sent to your mobile device, in addition to your password. Enable 2FA whenever possible to protect your accounts from unauthorized access.
3. Secure Your Home Network:
Protect your home network by changing the default login credentials of your router, using a strong Wi-Fi password, and encrypting your network. Limit access to your network and only give the password to trusted people only.
Also read: Top 10 Tips on How to Identify Phishing Emails and Links
4. Keep your Application/Software Up to Date:
Ensure to regularly update your operating system, web browsers, and applications is vital for preventing hacking. Software updates often include security patches that fix vulnerabilities that hackers could exploit.
5. Use Secure Wi-Fi Networks:
Avoid connecting to public Wi-Fi networks that are unsecured, as they can be easily compromised. You should rather use encrypted Wi-Fi networks with strong passwords, or consider using a virtual private network (VPN) for added security when accessing the internet on the go.
Suggested read: 16 Best Free VPN for Android, iPhone and Computer Users
Also read: 6 Ultimate Dangers of Using Free Public WiFi
6. Be Cautious of Phishing Attempts
Phishing attacks use deceptive emails, messages, or websites to trick users into sharing sensitive information. Be vigilant and avoid clicking on suspicious links, downloading attachments from unknown sources, and providing personal information to untrusted sources.
7. Practice Safe Browsing Habits:
Exercise caution while browsing the internet. Avoid visiting suspicious websites, downloading files from untrusted sources, and clicking on pop-up ads. Do not access or submit your information to websites that are not protected with SSL. You can also use ad-blockers to reduce the risk of encountering malicious content and hacking.
8. Use Firewalls and Antivirus Software:
Also, consider Installing antivirus software and enabling firewalls on your devices. These security measures act as barriers against malicious software, helping to detect and prevent hacking attempts.
Also read: 6 Password Safety Tips you Should Never Ignore
